Azure Active Directory login extensions and errors you can come across
I’ve been playing with the Azure Active Directory login extensions for both Linux and Windows in the past months and I’ve came across a few errors and problems I wanted to share with you.
But before sharing the problems with you, lets see how you can install the extension
Linux extension setup
As there as multiple ways to enable the extension, you can follow the documentation here.
If you are using ARM to deploy, use the following resource snippet
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 |
{ "type": "Microsoft.Compute/virtualMachines/extensions", "apiVersion": "2019-12-01", "name": "[concat(variables('vmName'),'/', 'AADLoginForLinux')]", "location": "[parameters('location')]", "dependsOn": [ "[resourceId('Microsoft.Compute/virtualMachines',variables('vmName'))]" ], "properties": { "publisher": "Microsoft.Azure.ActiveDirectory.LinuxSSH", "type": "AADLoginForLinux", "typeHandlerVersion": "1.0", "autoUpgradeMinorVersion":true } } |
Windows extension setup
Similarly, like the linux extension, you can following the documentation here.
If you are using ARM to deploy, use the following resource snippet
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 |
{ "type": "Microsoft.Compute/virtualMachines/extensions", "apiVersion": "2019-12-01", "name": "[concat(variables('vmName'),'/', 'AADLoginForWindows')]", "location": "[parameters('location')]", "dependsOn": [ "[resourceId('Microsoft.Compute/virtualMachines',variables('vmName'))]" ], "properties": { "publisher": "Microsoft.Azure.ActiveDirectory", "type": "AADLoginForWindows", "typeHandlerVersion": "1.0", "autoUpgradeMinorVersion":true } } |
Errors and problems
Along with the problems/troubleshooting that appears in the documentation, here is what I experienced.
Linux extension
The linux extension hasn’t given me a whole lot of problems. The only problem I encountered was when the DNS resolution on the VM that had the extension installed could not resolve hostnames. This made the extension fail when you tried to log in using your UPN (i.e your email).
Windows extension
The windows extension is more tricky. Here are the problems I encountered.
AzureSecureVMEnroll failed with 0x801c0001
AzureSecureVMJoinOperation: DeviceEnroller::AzureSecureVMEnroll failed 0x801c0001. AAD Join failed with status code -214564863
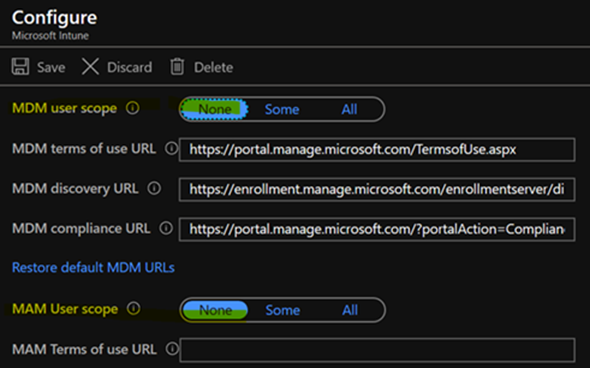
This error occurs when you have the MDM user scope (and/or the MAM user scope) set to Some or All. You need those scopes to be disabled for the VM to be able to be AAD joined.
To do this, navigate to the Azure Active Directory blade -> Mobility (MDM and MAM)
Select Microsoft Intune and set the MAM and MDM user scope to None.
If you have Microsoft Intune enrollment, do the same thing, that is set the MDM user scope to None.
User level MFA vs MFA in conditional access policies
When a user MFA is set using the “user level MFA” from https://account.activedirectory.windowsazure.com/UserManagement/MultifactorVerification.aspx?BrandContextID=O365 versus conditional access policies MFA in the AAD (from the azure portal), the user cannot login to the machine. A user capable of disabling the user level MFA from the link above, needs to disable the MFA for the user for it to work.
Sign-in through a Windows 10 PC that doesn’t use strong authentication
If a sign-in is done through a Windows 10 PC that doesn’t use strong authentication, it will not satisfy a conditional access policy that requires MFA to sign-in and need to bypass the strong authentication requirement by adding the Azure Windows VM Sign-in as an Excluded cloud application on the policy.
Extension install fails with -2145648639
If you have a Virtual Machine resource name that has more than 15 characters or that is already registered in the devices list in the Azure Active Directory, the AAD Join will fail. This is because Azure Device Registration Service finds the resource id parameter is invalid when it attempts to stamp the AzureResourceId value on the DevicePhysicalIds attribute of the device object.
You have no choice but to rename your virtual machine to have 15 or less characters and make sure the resource name is unique amongst the devices list in the Azure Active Directory.
Conclusion
Both the Linux and the Windows extensions are great, but the extension is still in public preview and such problems I’ve encountered aren’t documented. I’ve opened some GitHub issues (this, this and this) to update the documentation, but I am still waiting for them to take action.
Don’t be shy to comment on them to get them to update them ASAP. Also don’t be shy to open a UserVoice if you believe any of the problems I’ve mentioned should be fixed or at least be looked at by the product them (ahem 15 characters limit and MDM/MAM user scope).
UPDATE 2021-06-01: The AADLoginForLinux is being deprecated on 2021-08-15. Please use the new extension, SSH based, AADSSHLoginForLinux.
